
A Comprehensive Guide to Singapore Cybersecurity Compliance
Singapore’s digital infrastructure is governed by a robust set of cybersecurity frameworks. For companies
g

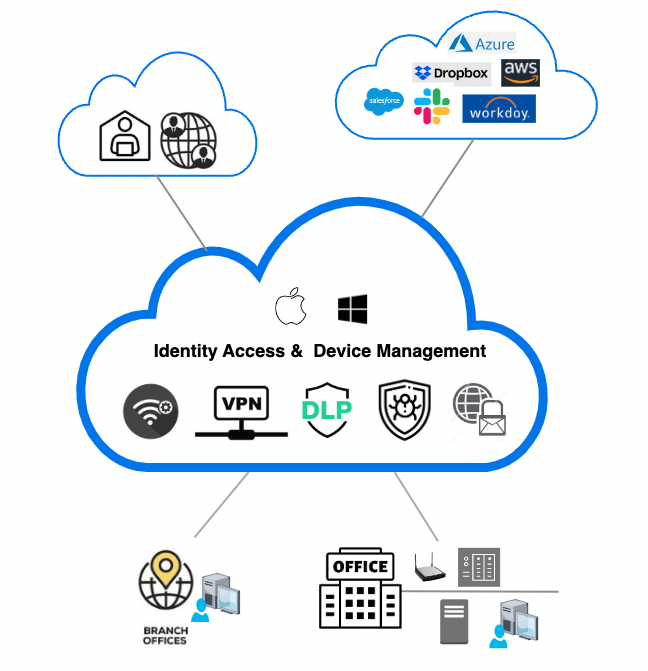
Support Windows & MacOS. Streamline application deployment, push out security policies, Anti-virus, DLP and VPN.

Control user access & devices, track Anti-Virus alerts, device compliance, VPN and DLP alerts all from a single admin console instead of using multiple tools
Effortlessly achieve and maintain compliance with MAS TRM, PDPA, or ISO27001, while meeting local data requirements (solution hosted on AWS Singapore)
100% intuitive Cloud based platform lets you securely manage, support and enforce compliance wherever your users are, as long as they are connected to internet
Complete cross-platform identity and device management for Windows, Mac and Linux, plus integrated Anti-Virus, where malware and virus alerts can be monitored on the same console.
Provides device baseline scanning to ensure continuous compliance
Satisfy MAS TRM with Identity, device, and access management.
Provides VPN that allows end users to connect to VPN tunnel with encryption for internal network access
Bundled with Secure Web Gateway that acts as an intermediary between users and the Internet for content inspection
It is a Software-as-a-Service (SaaS) that helps organizations manage and secure user identities, devices, and access to Company’s IT resources through the cloud. Unlike Windows Domain, there is no need to set up and maintain a hardware server for that purpose. You can easily scale as your Company grows.
Managing users and IT devices is essential for ensuring security, preventing unauthorized access, and protecting sensitive data. It helps enforce compliance, streamline device updates, and improve operational efficiency. Proper management also allows for quick onboarding, remote troubleshooting, and controlled access, safeguarding both the organization and its resources.
As a company grows, managing an increasing number of users, devices, and applications becomes difficult to enforce manually. This is where an Identity and Access Management (IAM) solution comes into play. A cloud-based IAM solution allows you to efficiently manage users and devices, no matter where they are located—ideal for today’s remote and distributed workforce
The short answer is Yes. Because of today’s increasingly mobile workforce and the ever-present prospect of compulsory work from home. A Domain laptop is no longer managed once it leaves the office, whereas an IAM-managed laptop is managed as long as it is connected to the internet.
Our IAM solution can manage devices side by side with MS AD, so that devices stay managed whether in or out of the office.
At the same time, it can also replace MS AD if you want to streamline your management platform.
Our Comply package covers almost all aspects of MAS TRM (Technology Risk Managment Guidelines).
From pushing out policies, applications, patching to Data Leak Prevention and enforcing and monitoring Cloud activities, It is specially tailored for Financial Institution to meet TRM requirements effortlessly.
Read more here
Yes, our solution is highly modular.
Additional modules such as Anti-Virus, SSO, DLP, VPN, Secure Web Gateway are available as add-on.
Just contact us via form or at sales@perennialconsultancy.com and let us know your requirements. We will work out a budget-friendly quotation for you.
Data Leak Prevention (DLP) solution is used to ensure that sensitive or confidential information does not leave an organization without proper authorization. It is designed to detect, monitor, and block the transmission of sensitive data—whether it’s through email, file transfers, or cloud storage—to prevent accidental or malicious data breaches.
CASB (Cloud Access Security Broker): A CASB is a security tool that acts as a gatekeeper between users and cloud applications, providing visibility, data protection, threat detection, and compliance enforcement for cloud services. It helps secure both sanctioned and unsanctioned (shadow IT) cloud use, ensuring that sensitive data is protected in the cloud.
SWG (Secure Web Gateway): An SWG protects users’ internet access by filtering and monitoring web traffic. It blocks malicious websites, prevents data loss, enforces acceptable use policies, and guards against web-based threats like malware and phishing, securing browsing activities whether users are in the office or remote.
Read more here

Singapore’s digital infrastructure is governed by a robust set of cybersecurity frameworks. For companies
In March 2025, a staggering security blunder rocked the Trump administration when top officials

In today’s digital world, many Small and Medium Enterprises (SMEs) in Singapore believe that