The Growing OT Cybersecurity Mandates for SG Government Projects
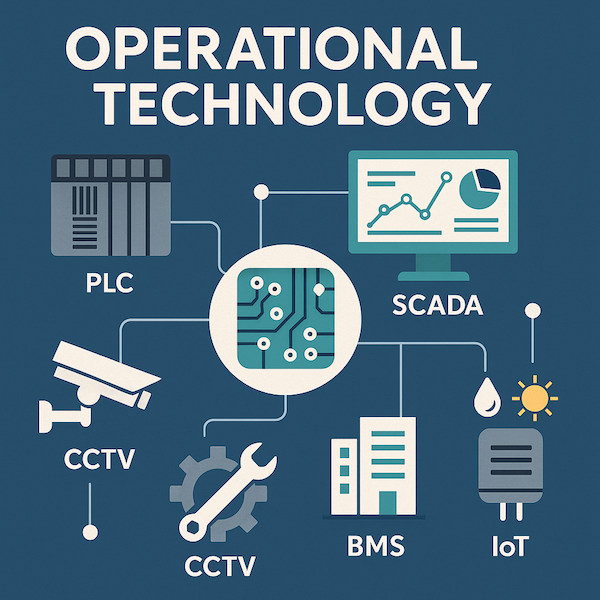
As more Mechanical & Electrical (M&E) vendors take on projects involving Operational Technology (OT) in critical infrastructure — from defense facilities to surveillance networks — cybersecurity is no longer optional. It’s a fundamental requirement. Whether you’re deploying SCADA systems for water treatment or installing sensors in a defense facility, your OT systems are now part…